DevOp Hacks
KASM HACKS:
- In 3-4 sentences, please explain the significance of virtual desktops and KASM. How can virtual desktops such as these be utilized in our AP CSP environment? (0.45)
KASM improves the security and protects a kernel address in an operating system. KASM creates a secure copy and effectively and efficiently detects unauthorized activity on the kernel as well. Virtual desktops is useful in managing different workflows and increasing productivity. It’s extremely conveninent for multitasking across multiple different computing environments.
- Attempt to work through the KASM setup with your team. Attach two screenshots to show that you have successfully gone through the setup: The first screenshot of KASM generating your credentials, and the second screenshot of the KASM workspace once you have logged in. (0.45)
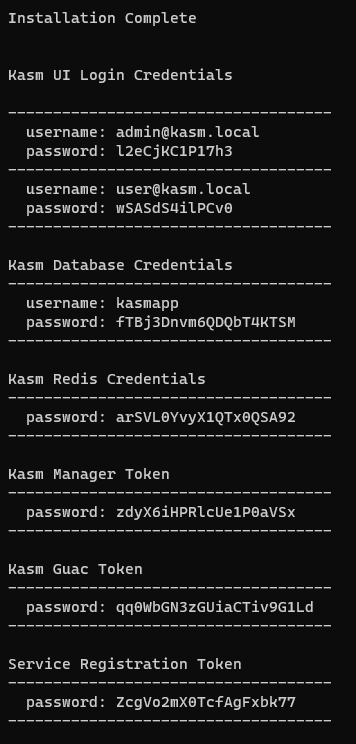
AWS DATABASES HACKS:
-
QUIZ: https://vardaansinha.github.io/devops/2023/04/23/DifferentAWS.html
-
QUIZ #2: https://vardaansinha.github.io/devops/2023/04/02/AWSSQL.html
QUIZ 1:
What is the main difference between relational and non-relational databases?
A. Relational databases are only used for structured data, while non-relational databases are only used for unstructured data.
B. Relational databases can easily handle high data volumes, while non-relational databases cannot.
C. Relational databases are based on tables and use SQL, while non-relational databases are based on collections and use JSON-like documents.
D. Relational databases are more expensive than non-relational databases.
Which AWS database service is best suited for applications that require low-latency speed?
A. Amazon ElastiCache
B. Amazon Neptune
C. Amazon DocumentDB
D. Amazon RDS
What is the purpose of the code example provided in the lesson?
A. To demonstrate how to create a table in Amazon Aurora.
B. To show how to query data from a DynamoDB table.
C. To provide an example of how to connect to a database instance in RDS using Python.
D. To showcase how to insert data into a MySQL table.
QUIZ 2:
Which of the following is not an AWS database option?
A. Amazon RDS
B. Amazon Neptune
C. SQLite
D. Amazon DynamoDB
Which of the following is a file-based, lightweight RDBMS?
A. Amazon RDS
B. Amazon Neptune
C Amazon DynamoDB
D. SQLite
Which AWS service enables you to store and query highly connected datasets?
A. Amazon Relational Database Service (RDS)
B. Amazon DynamoDB
C. Amazon Neptune
D. Amazon DocumentDB
DuckDNS and AWS HACKS:
- HACK 1: Create a diagram (Canva). What are the pros and cons of using DuckDNS? Show a diagram of an application running on AWS using a DuckDNS system.
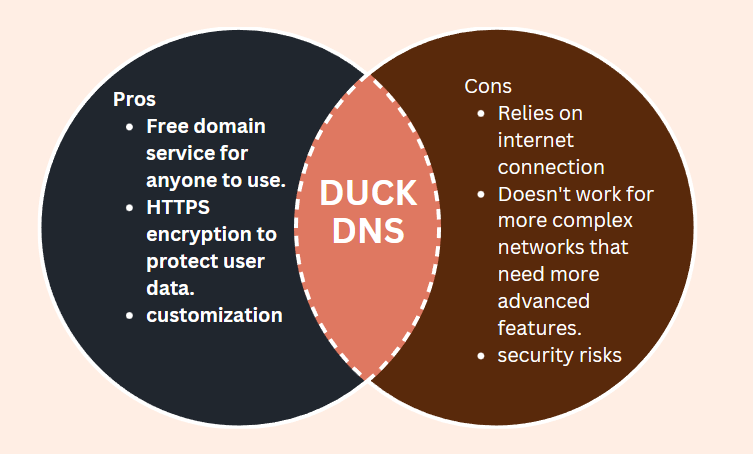
- HACK 2: Write a reflection. Why do we use DNS? How does DuckDNS work? What makes DuckDNS unique? How is DuckDNS useful for our projects? What are the steps to setup DuckDNS?
DuckDNS is a free DNS service that allows users to assign a domain name to a IP address. DuckDNS is unique because it is both free and easy to use and can be used to create custom domain names for your network, whereas other services require the user to pay. It’s useful for projects that require remote access to a home network, such as a flask or python web application. The steps to setting up Duck DNS are as follows:
(1) Sign in with your DuckDNS account by selecting “Sign in with Github” (2) Create a subdomain by entering a unique name and clicking “add domain” (3) Under “current ip”, change the IP address into the IP address that you would need (4) Click the “update ip” button to confirm the change (5) Use your unique DuckDNS subdomain
- HACK 4: In 2-3 complete sentences, talk about any outdated Nginx/Docker functionalities that may need to be addressed or any confusions you may have in regards to the deployment process from Trimesters 1 and 2.
I was initially uncertain about the distinction between the nginx sites-enabled directory and the nginx sites-available directory. At first, I assumed that these directories contained the same file content but with different file names, so I believed that the procedures could be applied interchangeably. Unfortunately, my assumption was incorrect, which led me to repeat the entire deployment process. Another issue that added to my confusion was the presence of red-colored font files in the nginx directories. Despite repeatedly deleting these files, they kept reappearing due to the shared EC2 instance used by everyone.
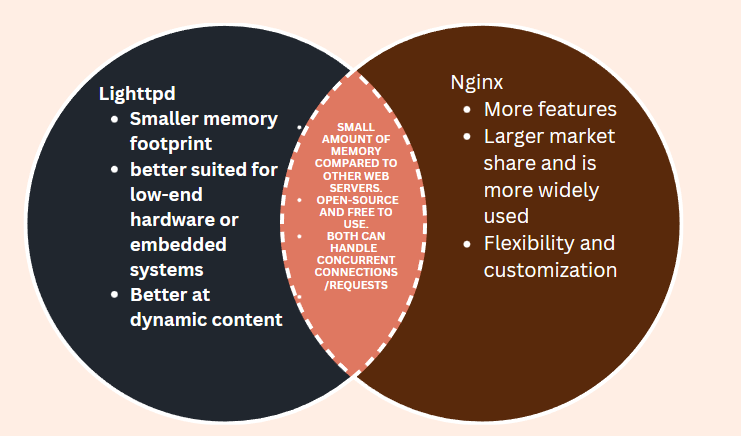
- HACK 5: Create a Venn Diagram comparing Nginx with Lighttpd.
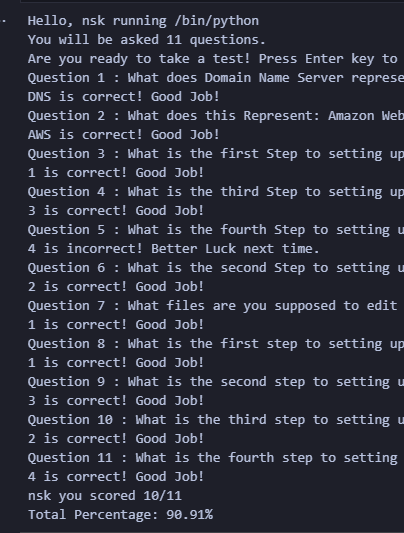
- HACK 6: Complete the Python quiz and attach your output from the notebook (should be done once you do the quiz.)
CERTBOT HACKS:
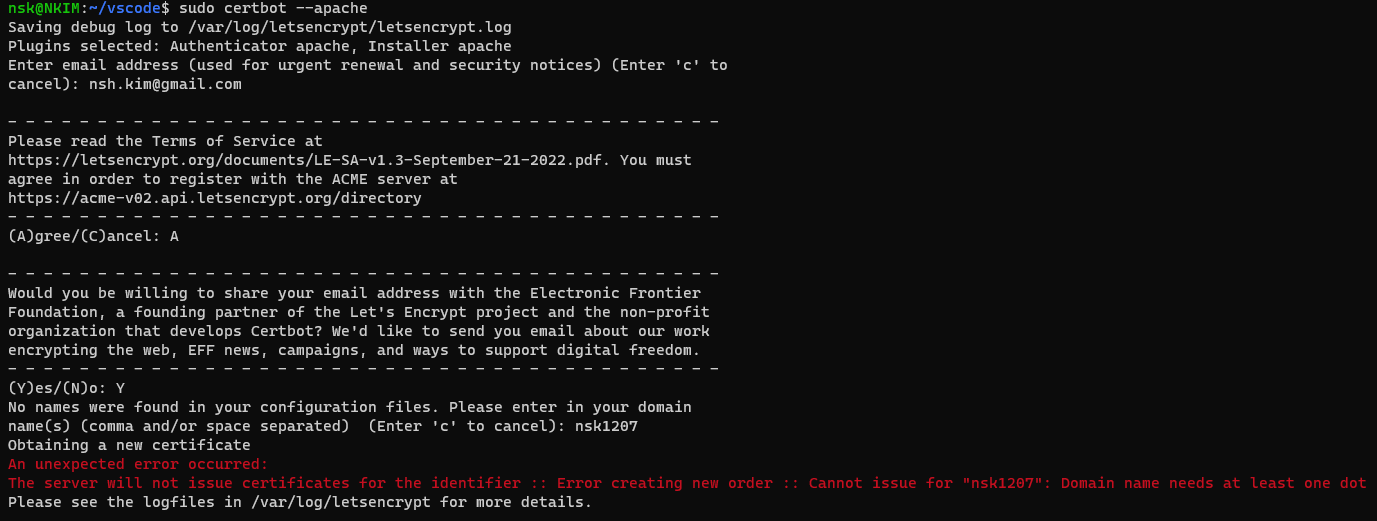
- Follow the instructions below and provide a full screenshot of all terminal commands after and including sudo certbot –apache all the way until it asks for the domain you want to secure. At this point you can take a screenshot and cancel the process. If you choose to continue the setup process and get Certbot fully working and show a before and after screenshot of your domain with http amd https connection we will grant extra credit points on hacks, or make up for lost points in other areas.
- Research and compare the security features of OpenSSL and LibreSSL, and write about the recent vulnerabilities within it. Write about your research in a fastpages blog post. It can be the same post that has your screenshot for the Certbot Hacks.
OpenSSL is a widely used library that provides support for a broad range of cryptographic algorithms, including symmetric encryption, asymmetric encryption, and hash functions. It is available for a wide range of operating systems and programming languages, including Linux, Windows, and mac. OpenSSL has a lot of vulnerabilities, including the notorious Heartbleed bug, which was discovered in 2014 and affected millions of websites. However, OpenSSL has since undergone significant code reviews and security audits, resulting in numerous improvements and bug fixes. LibreSSL is a fork of OpenSSL that was created in response to the vulnerability.
SCORING GUIDELINES:
As talked about in class, we’ll be looking for effort in the hacks. Though some setups may inevitably not work, we want to see that you took a stab at it and that you understand what the errors you’re getting might mean.
FOR 2/4 SECTIONS OF HACKS COMPLETE: HIGHEST WILL BE A 3.2/4 POSSIBLE –> 0.8/1
FOR 3/4 SECTIONS OF HACKS COMPLETE: HIGHEST WILL BE A 3.6/4 POSSIBLE –> 0.9/1
FOR 4/4 SECTIONS OF HACKS COMPLETE: YOU CAN GET UP TO A 4/4 –> 1/1